| 5 Things You Never Knew Your Cell Phone Could Do For all the folks with cell phones this should be printed and kept in your car, purse, wallet. Good information to have with you.There are a few things that can be done in times of grave emergencies. Your mobile phone can actually be a life saver or an emergency tool for survival. Check out the things that you can do with it: FIRST Emergency The Emergency Number worldwide for Mobile is 112. If you find yourself out of the coverage area of your mobile network and there is an emergency, dial 112 and the mobile will search any existing network to establish the emergency number for you, and interestingly, this number 112 can be dialed even if the keypad is locked. Try it out. SECOND THIRD FOURTH When your phone gets stolen, you can phone your service provider and give them this code. They will then be able to block your handset so even if the thief changes the SIM card, your phone will be totally useless. You probably won’t get your phone back, but at least you know that whoever stole it can’t use/sell it either. If everybody does this, there would be no point in people stealing mobile phones. And Finally…. FIFTH This is the kind of information people don’t mind receiving, so pass it on to your family and friends. |
| 11 Things To Never, Ever Say On Facebook Facebook is great for sharing the most special of life’s moments. Like pictures of a cake, funny links or your need for an able body to help you move a sofa. But those status updates are an open announcement to everyone you know. Some information is unwelcome. Some of it is unbearable. So, for the sake of all your friends, the following public statements are no longer allowed.
The birthday thank you Deaths Personal messages to your significant other Hangovers Now we know. Now we can nod solemnly and think: Man, you are the coolest, and you have the worst hangover of all time, and you vow to never drink again. Maybe you won’t mention it again, either. College admissions Exercise Asking for money Romantic anniversaries New phone number Bemoaning Facebook Engagements When it doubt, use the golden rule. Stay away from things nobody but you cares to know about or celebrate. Then, Facebook will continue to be a fire hose of semi-interesting life gristle, instead of a dump truck full of tripe. |
Microwaving Water! A 26-year old man decided to have a cup of coffee. He took a cup of water and put it in the microwave to heat it up (something that he had done numerous times before). I am not sure how long he set the timer for, but he wanted to bring the water to a boil.. When the timer shut the oven off, he removed the cup from the oven. As he looked into the cup, he noted that the! Water was not boiling, but suddenly the water in the cup ‘blew up’ into his face. The cup remained intact until he threw it out of his hand, but all the water had flown out into his face due to the buildup of energy. His whole face is blistered and he has 1st and 2nd degree burns to his face which may leave scarring.He also may have lost partial sight in his left eye. While at the hospital, the doctor who was attending to him stated that this is a fairly common occurrence and water (alone) should never be heated in a microwave oven. If water is heated in this manner, something should be placed in the cup to diffuse the energy such as a wooden stir stick, tea bag, etc…, (nothing metal).General Electric’s Response:Thanks for contacting us, I will be happy to assist you. The e-mail that you received is correct. Microwaved water and other liquids do not always bubble when they reach the boiling point. They can actually get superheated and not bubble at all. The superheated liquid will bubble up out of the cup when it is moved or when something like a spoon or tea bag is put into it.To prevent this from happening and causing injury, do not heat any liquid for more than two minutes per cup. After heating, let the cup stand in the microwave for thirty seconds! Before moving it or adding anything into it.Here is what our local science teacher had to say on the matter: ‘Thanks for the microwave warning. I have seen this happen before. It is caused by a phenomenon known as super heating. It can occur anytime water is heated and will particularly occur if the vessel that the water is heated in is new, or when heating a small amount of water (less than half a cup). What happens is that the water heats faster than the vapor bubbles can form. If the cup is very new then it is unlikely to have small surface scratches inside it that provide a place for the bubbles to form. As the bubbles cannot form and release some of the heat has built up, the liquid does not boil, and the liquid continues to heat up well past its boiling point. What then usually happens is that the liquid is bumped or jarred, which is just enough of a shock to cause the bubbles to rapidly form and expel the hot liquid. The rapid formation of bubbles is also why a carbonated beverage spills over when opened after having been shaken.’ If you pass this on you could very well save someone from a lot of pain and suffering! |
| 7 Clever Google Tricks Worth Knowing Below are compiled a list of 7 clever Google tricks that I believe everyone should be aware of. Together I think they represent the apex of the grand possibilities associated with Google search manipulation tricks and hacks. Although there are many others out there, these 7 tricks are my all-time favorite. Enjoy yourself.
1. Find the Face Behind the Result – This is a neat trick you can use on a Google Image search to filter the search results so that they include only images of people. How is this useful? Well, it could come in handy if you are looking for images of the prominent people behind popular products, companies, or geographic locations. You can perform this search by appending the code &imgtype=face to the end of the URL address after you perform a standard Google Image search.
2. Google + Social Media Sites = Quality Free Stuff – If you are on the hunt for free desktop wallpaper, stock images, WordPress templates or the like, using Google to search your favorite social media sites is your best bet. The word “free” in any standard search query immediately attracts spam. Why wade through potential spam in standard search results when numerous social media sites have an active community of users who have already ranked and reviewed the specific free items that interest you. All you have to do is direct Google to search through each of these individual social media sites, and bingo… you find quality content ranked by hundreds of other people.
3. Find Free Anonymous Web Proxies – A free anonymous web proxy site allows any web browser to access other third-party websites by channeling the browser’s connection through the proxy. The web proxy basically acts as a middleman between your web browser and the third-party website you are visiting. Why would you want to do this? There are two common reasons:
There are subscription services and applications available such as TOR and paid VPN servers that do the same thing. However, this trick is free and easy to access from anywhere via Google. All you have to do is look through the search results returned by the queries below, find a proxy that works, and enter in the URL of the site you want to browse anonymously.
4. Google for Music, Videos, and Ebooks – Google can be used to conduct a search for almost any file type, including Mp3s, PDFs, and videos. Open web directories are one of the easiest places to quickly find an endless quantity of freely downloadable files. This is an oldie, but it’s a goodie! Why thousands of webmasters incessantly fail to secure their web severs will continue to boggle our minds.
5. Browse Open Webcams Worldwide – Take a randomized streaming video tour of the world by searching Google for live open access video webcams. This may not be the most productive Google trick ever, but it sure is fun! (Note: you may be prompted to install an ActiveX control or the Java runtime environment which allows your browser to view certain video stream formats.)
6. Judge a Site by its Image – Find out what a site is all about by looking at a random selection of the images hosted on its web pages. Even if you are somewhat familiar with the target site’s content, this can be an entertaining little exercise. You will almost surely find something you didn’t expect to see. All you have to do is use Google’s site: operator to target a domain in an image search. 7. Results Based on Third-Party Opinion – Sometimes you can get a better idea of the content located within a website by reading how other websites refer to that site’s content. The allinanchor: Google search operator can save you large quantities of time when a normal textual based search query fails to fetch the information you desire. It conducts a search based on keywords used strictly in the anchor text, or linking text, of third party sites that link to the web pages returned by the search query. In other words, this operator filters your search results in a way such that Google ignores the title and content of the returned web pages, but instead bases the search relevance on the keywords that other sites use to reference the results. It can add a whole new dimension of variety to your search results.
Bonus Material: Here is a list of my favorite Google advanced search operators, operator combinations, and related uses:
|
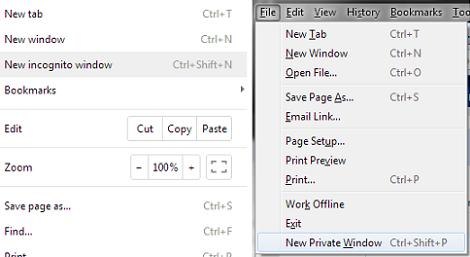
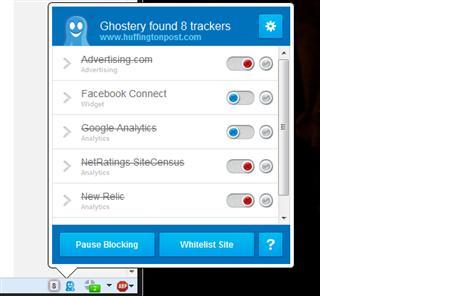
6 things you can do now to be stealthier on the Internet While being invisible on the Internet is about as possible as being invisible in real life, a few easy changes of habit can make you a more elusive target for advertisers, intrusive social networks and possibly even the NSA and friends. While these are measures anyone can take, please note, they won’t necessarily provide total anonymity or protection from hackers. They’ll just keep much of your everyday Internet activity from being recorded and tracked. 1. Use private browsing windows Google / Mozilla Private browsing on Chrome (left) and Firefox (right). Look for the option in the main menu of your browser. In Chrome it’s “Incognito,” in Firefox it’s “Private Window,” and in Internet Explorer it’s “InPrivate Browsing.” 2. Adjust your preferences! Sending anonymous usage data? Can it really be anonymous? Uncheck. Geotag pictures? You can always add location later. Uncheck. Check for updates on startup? Do you really want companies knowing exactly when and how often you use their stuff? Uncheck. How much information you volunteer is up to you, but usually you have to opt out rather than in. 3. Download browser plugins Ghostery Ghostery: Creeped out by Facebook widgets showing which of your friends likes the site you’re on? Ghostery allows you to turn on and off everything from social widgets to tracking cookies. HTTPS Everywhere: This useful tool from the Electronic Frontier Foundation makes sure you’re connecting with websites at the highest level of security supported, so it’s more difficult for snooping software to see what you see. It’s especially good if you use public Wi-Fi a lot. 4. Use false identities It’s not just your name that you should be careful with, either. Your username is often public-facing, and can be used to track you as well. Are you “SeattleGuy1949″ on Gmail, AIM and assorted support forums? Advertisers (and hackers) will be able to connect the dots. Make up unique names, and let a password manager — or a pad of paper — take care of remembering them. Lastly, there’s no reason to have everything go to your main email address. Email is free, so keep one for personal correspondence and a spare for lists and sign-ups. Some email services, such as Microsoft’s Outlook.com, let you add additional email addresses — and even temporary ones — for transactions you want to keep one-sided. 5. Choose services built for anonymity Try these alternatives to the usual suspects: DuckDuckGo DuckDuckGo search engine provides solid results, totally anonymously. Unsurprisingly, the site’s traffic has skyrocketed since the PRISM story broke. Hushmail works like any other webmail, but offers strong encryption both while your emails are in transit and when they’re stored. The host company won’t look unless a court order forces them to. (Note: If you love your current webmail, you may be able to deactivate the ad-tracking, so have a look in the preferences before jumping ship.) SpiderOak cloud storage is totally encrypted — only you know what you put there. If 2GB is enough for your private files, sign up for a free account and you can be reasonably sure that your data is secure. 6. Take extreme measures That said, for most of the everyday surveillance we’re subjected to as we use Internet services and browse the Web, the rest of the above should help keep you undercover. |
This Is The Greatest Keyboard Shortcut Ever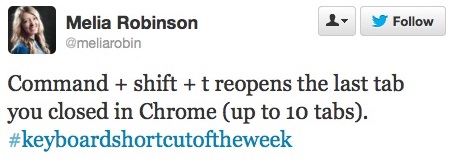 That’s for Mac users. If you’re on a PC, it’s Ctrl+Shift+T. That’s for Mac users. If you’re on a PC, it’s Ctrl+Shift+T.
Try it right now. Close this tab and bring it back. I dare ya. See how cool that was? This miraculous finger-to-keyboard resuscitation, a sort of Ctrl-Z for the entire Internet, means no more called-out cusswords, no more wishing the back button had you covered when, aiming to click on a tab, you accidentally hit the little X on the tab’s starboard. With just one more step than the Ctrl-T that gives new tabs life, the E*Trade tab you mistakenly closed will pop back into existence, all cued up to sell those 10,000 shares of stock. Don’t worry, the trick works in Firefox and Internet Explorer, too, so clumsy mousing won’t send your long political post on your uncle’s Facebook page on a one-way trip to the undiscovere’d country in those browsers, either. |
 |
Ted: 10 Top Time-Saving Tech Tips